Getting locked out of your online account can be annoying, but at the very least, it’s there to keep your account safe. However, as good as it may be to prevent hackers from trying to barge through the front door, it’s not perfect. So, how does this technology work, and how can hackers beat it?
What Is a Login Attempt Limiter?
If you’ve ever entered the wrong password into a website too many times, you’ll be very familiar with login attempt limiters. These restrict you to a certain number of logins in a period of time—they usually give you three attempts, but there’s no hard and fast rule about how many tries you get.
If you fail to enter the correct password enough times, the website will prevent logins to the account for a set amount of time. This method prevents hackers from using a brute force attack, where they spam passwords until one lets them in.
How Hackers Can Dodge Login Attempt Limiters
As useful as this technology is, it’s by no means impervious. There are ways hackers can get around this technology and access your account.
Brute Forcing Passwords Offline
Login attempt limiters only work because the website controls the number of attempts people can make when entering a password. If hacker removes the website from the equation and takes the passwords, they can brute force it for as long as they want.
Hackers will usually achieve this by breaking into a website’s security, finding where the downloads are stored, and saving it to their device. Once it’s there, they can start working on trying to crack the security. If a company has its password database stolen, it’s likely that login attempt limiters are the least of your worries.
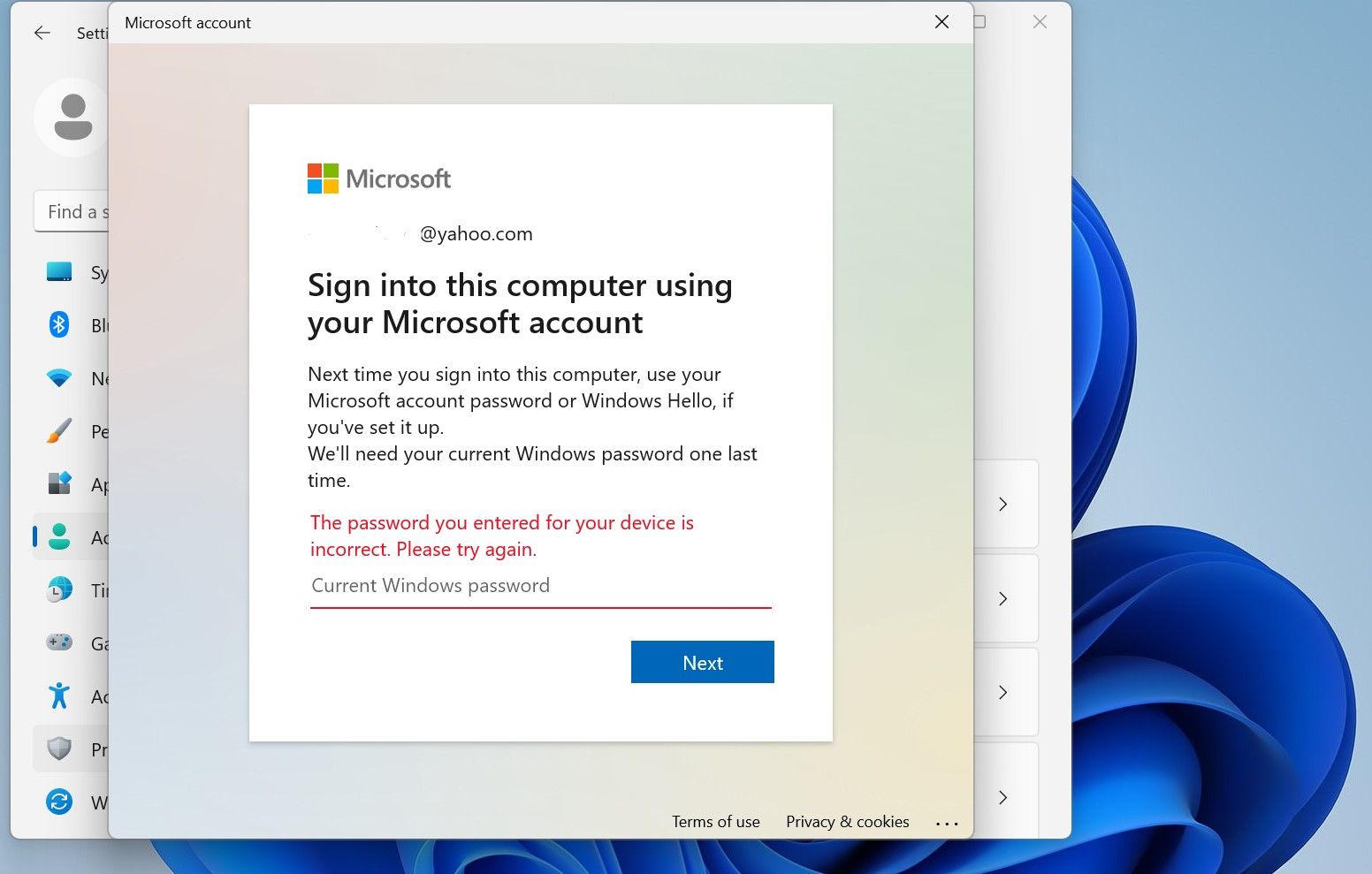
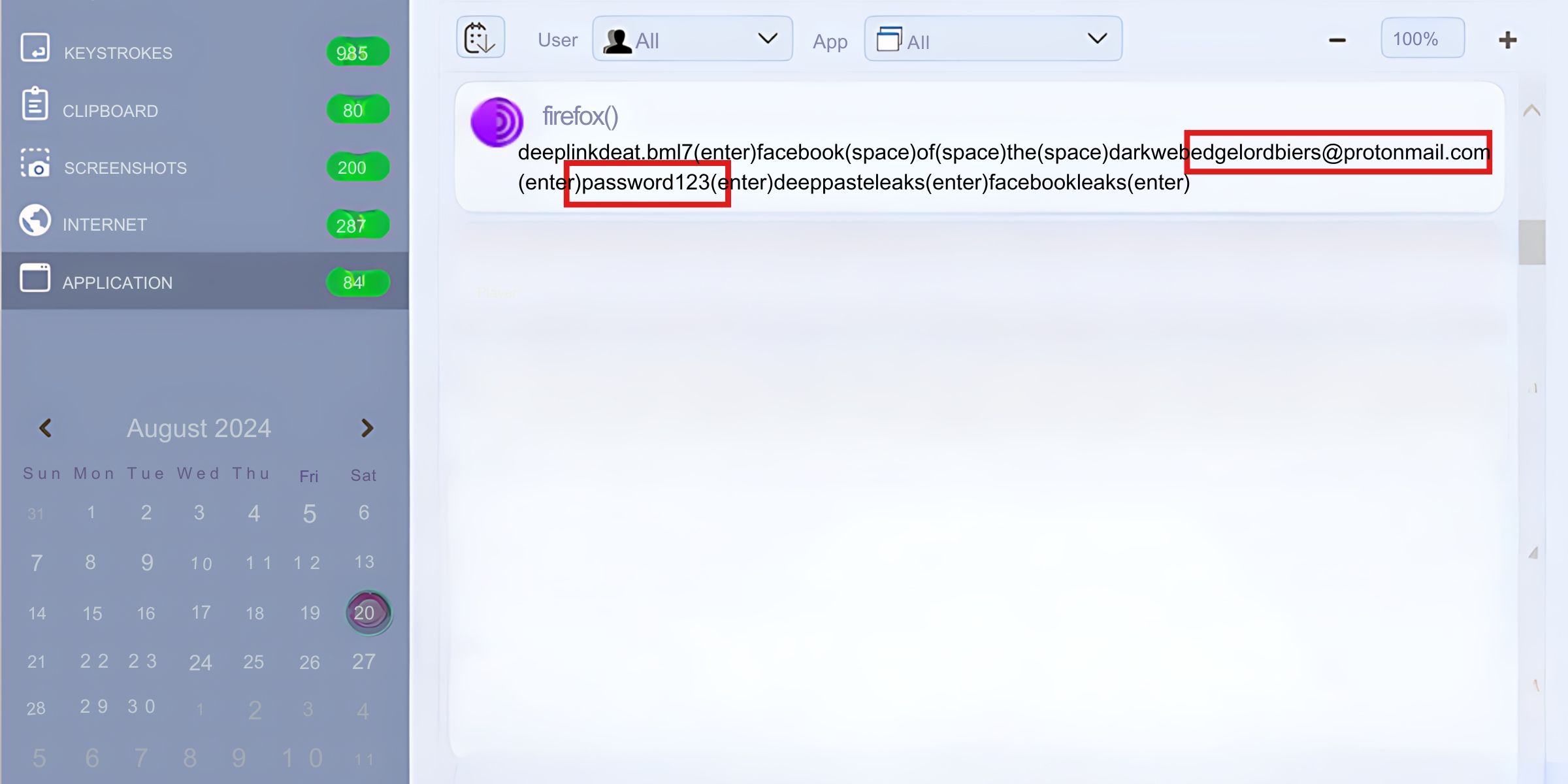
Stealing the Password via Malware
While login password limiters are good at defending against random attempts, they’re useless if the hacker knows the password beforehand. Credential stealing malware is a favorite tactic of bad actors, and if malware manages to get onto your computer, the hacker won’t need to guess what your password is—you’ll end up handing it over yourself.
Check out what keyloggers are for more information on how hackers can see what you type.
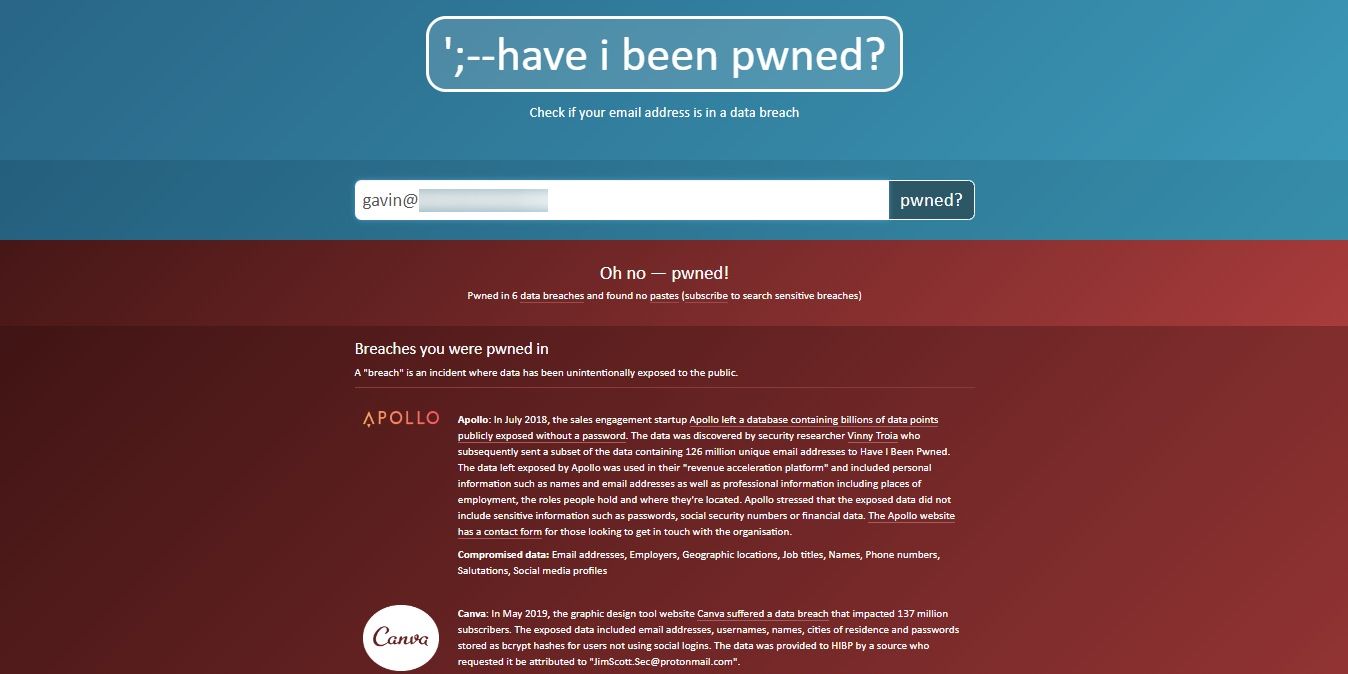
Re-Using Passwords From Prior Leaks
Password leaks are already devastating enough; if left unchecked, they can give hackers unfettered access to your account. But what’s even worse is if a password leak reveals a password you use for your other accounts.
If you re-use your passwords, it will only take one leak for a hacker to get a ‘skeleton key’ to all of your passwords. Once that happens, no amount of login limiters can save you; a hacker can waltz into all of your online accounts without resistance.
Check out the dangers of password recycling and how to mitigate it for more information.
Getting Your Password via Social Engineering
If a hacker really wants to get your password, they can try using social engineering. This is when a bad actor pretends to be someone they’re not in an attempt to trick you into giving them your password. This usually involves impersonating a boss, an admin, or tech support.
Read up on what social engineering is to help protect yourself from this form of attack.
How to Secure Your Account Against Hackers
Fortunately, while login attempt limiters aren’t perfect, there are methods to protect your accounts in case they fail. If you use strong passwords, use a different password for each account, and add two-factor authentication (2FA), you can make it really hard for someone to crack into your account.
If you follow everything we covered in our guide on how to secure your online accounts, you can ensure that any hackers trying to break into your account have a tough time getting in—if they ever do.
As useful as login attempt limiters are, they also have their own limits. Fortunately, you can do your part so that if this useful line of defense fails, hackers won’t have access to all of your online accounts.