Major data leaks potentially exposing your data to evildoers have become a daily occurrence. The easiest way to protect yourself, even if your passwords become known, is with two-factor authentication—but not all multi-factor authentication methods are created equal.
The 3 Best MFA Methods
Just because MFA provides an extra layer of security doesn’t mean cybercriminals cannot bypass MFA and access your data. That being said, if you’re using one of these methods, odds are slim that they’ll be able to crack the code.
Physical Security Key
Imagine if you could access your computer like you open your home– with a key. A physical security key is a tangible key that, once inserted into the USB port, grants you access to your computer. However, the major downside to using a physical security key is that accessing your device becomes a rather tricky process if you lose it.
It’s worth mentioning that there are two types of security keys: Bluetooth and USB. While both are incredibly secure, a Bluetooth-capable physical security key may be susceptible to man-in-the-middle attacks in which the password sent over Bluetooth is stolen. Such an attack is not possible when using a USB-capable security key.
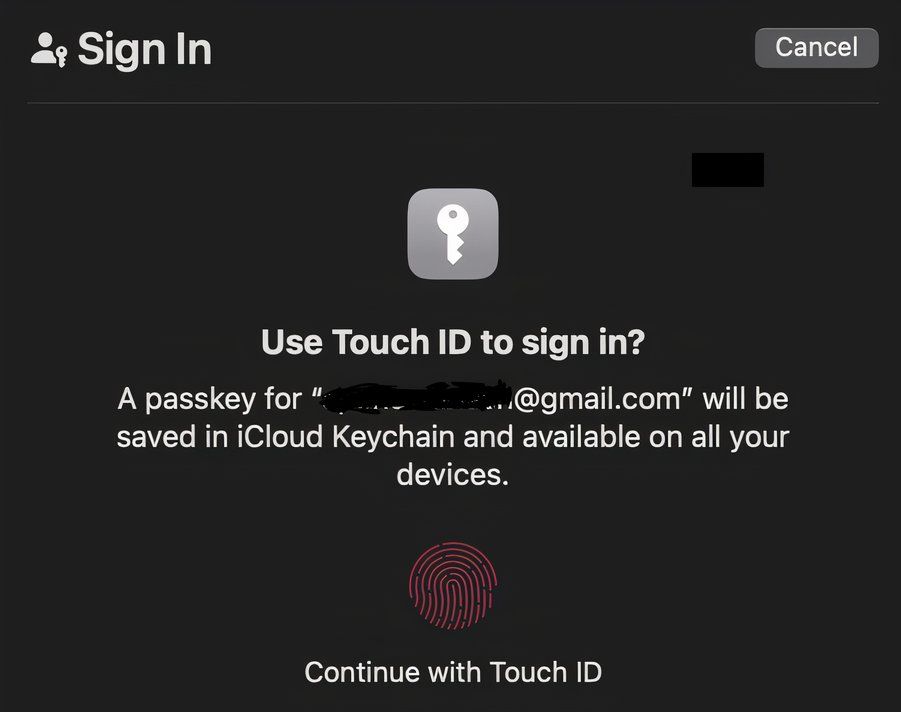
Biometric Authentication
What if instead of carrying around a key in your pocket, you were the key? Biometric authentication entails using a part of your body to provide authentication. Popular biometric methods include using one’s face, fingerprint, voice, handwriting, and vein patterns.
Biometric authentication has become popular in recent years ever since Apple introduced Touch ID in 2013 (Android devices also received fingerprint biometrics in 2014, with Android 4.4). Many have started using biometrics to provide authentication because it’s easy to use and incredibly secure. Unlike a physical key that can be lost or stolen, chances are you won’t forget your finger in the restaurant anytime soon.
One-Time Password (Authenticator App)
One-time passwords (OTPs) are unique, single-use passwords that must be used within a certain time frame before expiring. There are various ways to receive OTPs, but the most secure is through an authenticator app such as Google Authenticator.
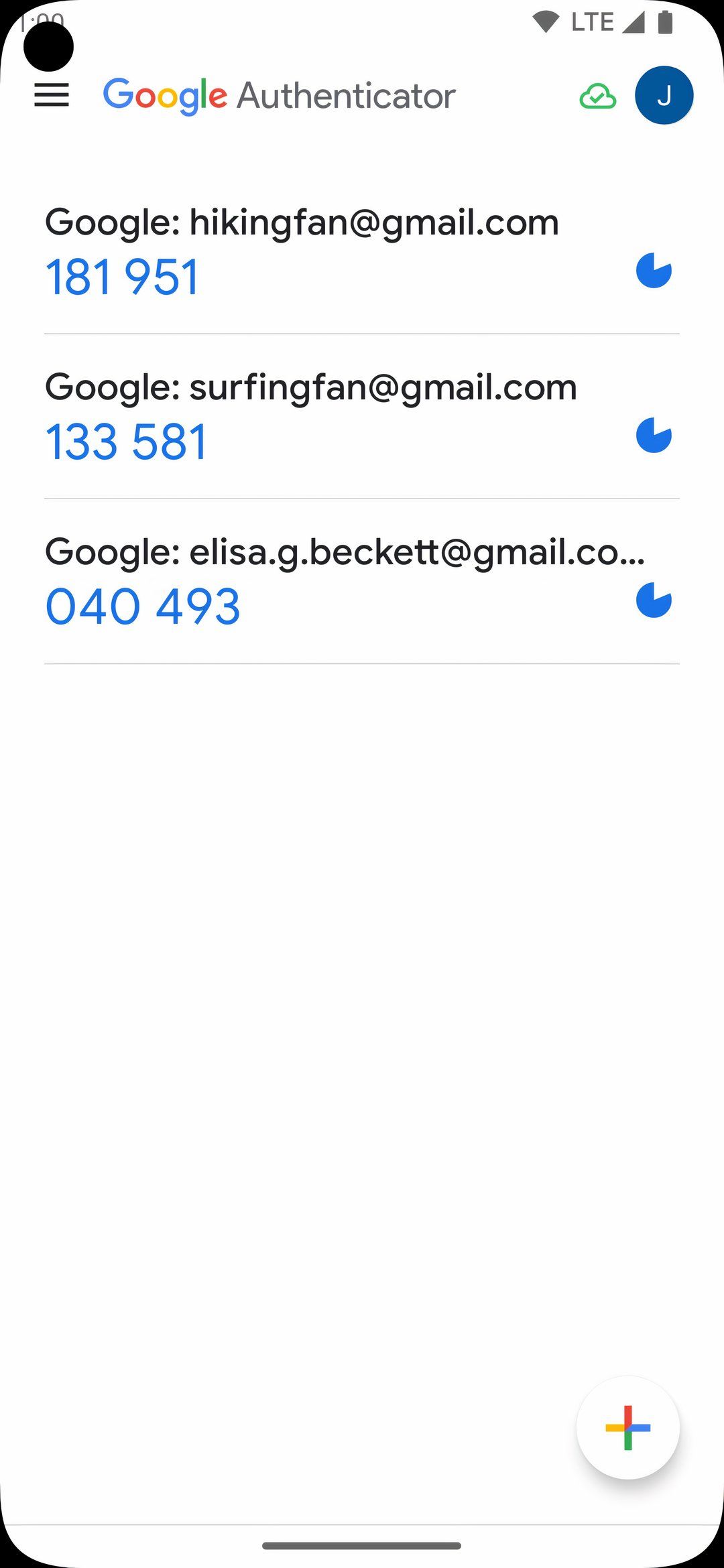
With Google Authenticator, you have up to 60 seconds to type in the OTP before a new one is generated. Not all OTP methods are as safe as one another. As we will see later on, OTPs sent via SMS and email are not nearly as secure.
Other MFA Methods
Using any MFA method is better than using none. That being said, certain methods are better than others. Here are the best of the rest.
Push Notification
Along with alerting you that you’ve received a new IG message or promotional offer, push notifications can also be used for security purposes. When activated, push notifications will be sent through the app of your choice and must be approved or denied. What’s nice about push notifications is that they do not require typing in characters the same way for example an authenticator app might.
Push notifications are user-friendly, offer strong security, and are fast. The chief vulnerability is that if your device is ever lost or stolen, the thief only needs to have access to your opened phone to authenticate with a push notification, which they do.
Phone Call
Let’s say you’ve already logged into your bank account but have enabled 2FA through a phone call. As soon as you type in your correct username and password, you will receive a phone call to the number on file and be provided with a second password. This method is safe enough if you have access to your phone, however a phone can easily be stolen or lost. Not to mention that most phone calls are not encrypted. If a skilled hacker is targeting you, they may listen to your calls. Having just been sent an unencrypted password, they can easily steal your password and gain access to your account.
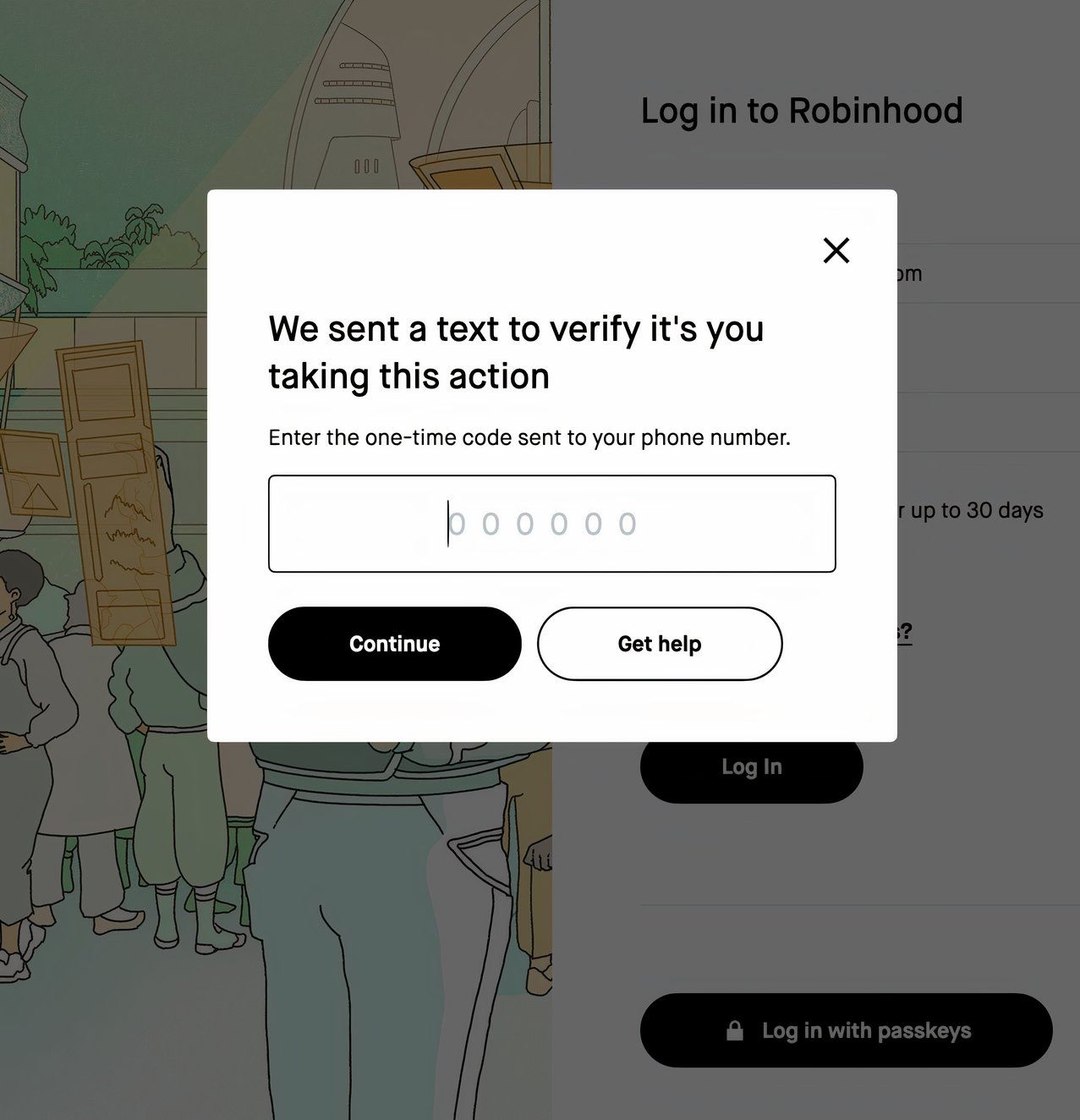
One-Time Password (SMS or Email)
OTPs sent over SMS or email are not unsafe; however, they are one of the least safe ways to authenticate a user. SMS and email OPTs are appealing because they are both simple and easy to implement. Less savvy tech users may not want to set up an authenticator app, know how to (or want to) enable biometric authentication, or even know what a physical security key is.
The issue is that SMS and even email can be compromised. 2FA is of little use if the second password is being sent to a cybercriminal. SMS messages can also be sent unencrypted and intercepted.
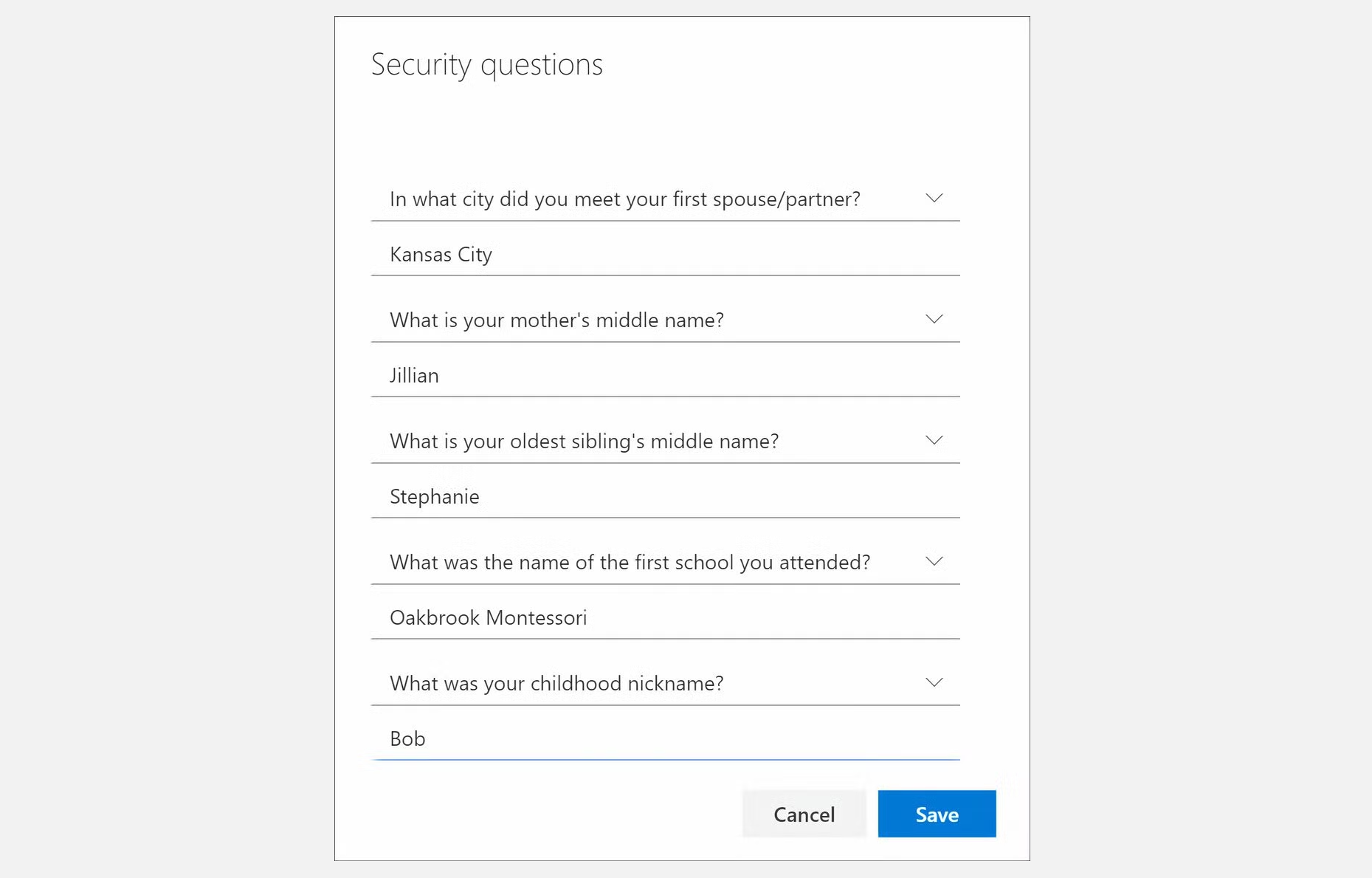
Security Questions
We have all filled in security questions at one time or another. Common security questions ask what your mother’s maiden name is, the name of your pet, and where you were born. The issue with these questions is that anyone viewing your Facebook account can probably find out this information. Another major problem is that these answers may be forgotten. Passwords and usernames are usually written down, whether in a password manager or elsewhere; however, answers to security questions are not. If you forget an answer, cybercriminals won’t be able to access your account, but neither will you.
You have many multi-factor authentication methods to choose from. Now that you know which ones are safest you can make a more informed decision about how to best protect your data. Regardless of your chosen method, remember that any 2FA is better than none.